RPV from Google One – Additional online security for your phone, VPN Google One – Reinforced online security for your phone
Strengthen your online safety with the Google One VPN
With the RPV Google One, you can enhance Google’s world caliber security by encrypting your online activity, regardless of the app or the browser you use.
Raise your safety online with the RPV Google One
You can encrypt your activity online to take advantage of an additional protective and confidentiality layer on Android, iOS, Windows and Mac devices.
RPV is only offered in some countries.
Additional online protection
With the RPV Google One, you can enhance Google’s world caliber security by encrypting your online activity, regardless of the app or the browser you use.
- therefore Reduce online follow -up by masking your IP address
- therefore Protect yourself against spying by computer hackers on unsecured networks (such as public Wi-Fi)
- therefore Browse the web with a private and secure connection 1
Trustworthy security
Confidentiality and security are at the heart of everything we design.
- therefore Google will never use the RPV connection to follow, journal or sell your navigation activity. 2
- therefore Advanced security is integrated into our systems. Thus, no one can use the RPV to link your online activity to your identity.
- therefore Do not just believe us: our customer libraries are free, and our end -to -end systems are verified independently.

Rapid performance
The RPV Google One is supported by the high -end network architecture of Google. RPV can be permanently activated and allows you to maintain a quick internet connection with all your apps, all your browsers and all your services.
Easy to use and shareable
Easily activate the RPV Google One and share access with your family group, even if group members use other operating systems.
- therefore You can activate RPV on all your Android, iOS, Windows and Mac devices
- therefore Five other people can take advantage of RPV protection when you share your package.
![]()
Operation of an RPV
Your browser and applications can frequently communicate confidential information online. Some sites and applications use obsolete or low encryption, or do not use it at all.
During the transfer, unsecured data can be intercepted by computer hackers, which compromises your confidentiality and your security as a whole.
When you activate an RPV, your online data is protected thanks to a transfer to a highly encrypted tunnel.
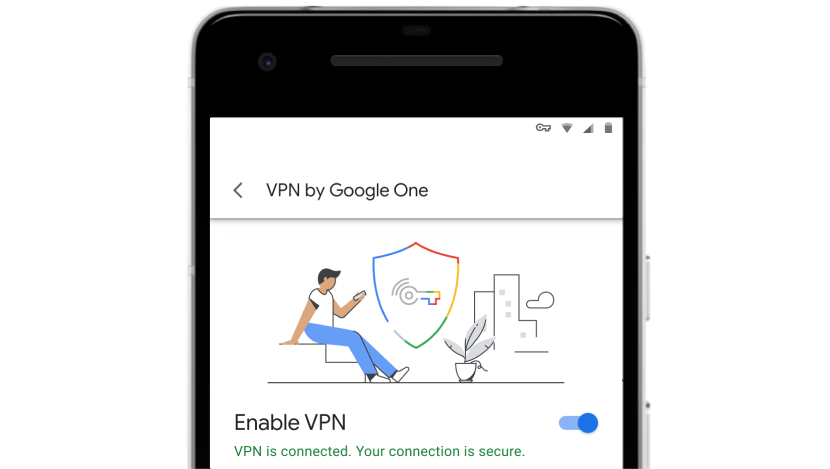
Start using the RPV Google One
Become a Google One member to enjoy the RPV Google One, offered with all the packages in some countries.
Activate the RPV in a single touch from the Google One application for Android and iOS, or from desktop applications for Windows and Mac 3 .
1 You will not be able to change the position of your IP address to see content that is not offered in your region.
2 A minimum quantity of journalization is made to ensure the quality of service, but your network traffic is never journalized, and your IP address is not associated with your activity.
3 To find out more about compatible operating systems versions, see this page.
Strengthen your online safety with the Google One VPN
You can encrypt your online activity to benefit from an additional level of protection and confidentiality on Android, iOS, Windows and Mac devices.
Subscribe to Google One
VPN available only in some countries.
Additional online protection
With the Google One VPN, you can strengthen Google’s advanced security by encrypting your online activity, regardless of the application or browser you use.
- therefore Reduce online follow -up by masking your IP address
- therefore Protect yourself from IT pirate listening to unsecured networks (such as public Wi-Fi).
- therefore Navigate the web with private and secure connection 1

Security with confidence
Confidentiality and security are at the heart of all the tools we create.
- therefore The VPN connection will never be used by Google to follow, record or sell data related to your navigation activity 2
- therefore Our systems incorporate advanced security features to ensure that no one can use VPN to associate your activity online with your identity.
- therefore You don’t have to believe us about it. Our client libraries are available in open source, and our end -to -end systems are subject to an independent audit.

High performance
The Google One VPN is based on Google’s network architecture, whose reputation is well established. Even if you are running the VPN permanently, you continue to benefit from a quick internet connection on all of your applications, browsers and services.
Simple and shareable
Easily activate the Google One VPN and share access with members of your family group, even if they use other operating systems.
- therefore You can activate VPN on all your Android, iOS, Windows and Mac devices
- therefore Five other people can take advantage of protection with the VPN if you share your package
![]()
How does a VPN work ?
Your browser and applications can regularly exchange sensitive information online. Some applications and some sites use obsolete or insufficient, even non -existent encryption.
During their routing, unsecured data can be intercepted by hackers, which can compromise the confidentiality of your data and your security as a whole.
When you activate a VPN, your online data is protected by borrowing a quantified tunnel.
Start using the Google One VPN
Become a Google One member to benefit from the Google One VPN, available with all packages in some countries.
Activate the VPN with a simple gesture in the Google One application for Android and iOS, or in desktop applications for Windows and Mac 3 .
Subscribe to Google One
1 You will not be able to modify the location of your IP address to consult content that is not available in your region.
2 A minimum journalization is carried out to ensure the quality of service, but your network traffic is never recorded and your IP address is not associated with your activity.
3 Consult this page to find out the compatible operating system versions.



