DNS Over Https and DNS Over TLS – Guides | Mullvad VPN, DNS leaks prevention | Proton VPN
Vite the DNS leaks
If Android is unable to connect to the dns then the dns server that you are road to are likely too far away and the latency is prohibitive. In this case it will not work.
DNS Over https and DNS Over TLS
OUR ENCRYPTED PUBLIC DNS DNS SERVICE DNS OVER HTTPS (DOH) and DNS OVER TLS (DOT). This Protects Your Dns Queries From Being Snooped On By Third parts when not connected to our vpn service as your dns quies are encrypted between your Device and our dns server.
This service is primary meant to be when you are disconnected from our vpn service, or on devices where it’s not possible or desirable to connect to the vpn. When you are already connected to our vpn service the Security Benefits of Using Encrypted Dns is Negligible and It Will Always be Slower Than Using the DNS Resolver on the VPN Server that you are connected to.
You can use this privacy-enhancing service in the fact if not a mullvad customer.
What This Guide Covers
- Mullvad Encrypted DNS Service Features
- Specials
- How to use this service
- – Web Browsers
- – Operating Systems
- How do I Know It’s Working?
- DNS Server Rentals
- How the Content Blocking Works
- Notes
Mullvad Encrypted DNS Service Features
This service provids Encrypted dns quries with the following features:
- Happy blocking: We provide Basic Content Blocking Options to Block Ads, Trackers, Malware, Adult Content, Gambling and Social Media.
- QNAME Minimization: This enables our dns servers to resolve your queries while giving it as little information as possible about the queries to other dns servers involved in the resolving process.
- AnycaSsed Service: Multiple mullvad servers in different rentals are configured to provides the same dns service. Your dns quries are meant to be road to the geographically closest server, Although peering and routing between internet providers might affect this. Should the Server Closest to you be Complely Offline Your Queries Will Be Road to the Second-Closest and So On On.
A LIMITED DNS RESOLVER IS LISENING ON PORT UDP/TCP 53 ONLY TO AID WIT.mullvad.Net, Adblock.mullvad.net and so on) so that Customers Can First Resolve the IP of the Resolver Before Querying It Over Encrypted DNS.
To Learn More about the Technologies in the Service See The Links Below.
- Wikipedia: Anycast
- Wikipedia: DNS Over TLS
- Wikipedia: DNS Over https
- QNAME Minimization
Specials
Hostnames and content blockkers
The Table below shows the different hostname options and their content blockkers. Return to this when configuring the dns with the instructions below.
| Hostname | Ads | Trackers | Malware | Adult | Gambling | Social Media |
|---|---|---|---|---|---|---|
| dns.mullvad.net | ||||||
| adblock.dns.mullvad.net | ✅ | ✅ | ||||
| base.dns.mullvad.net | ✅ | ✅ | ✅ | |||
| extended.dns.mullvad.net | ✅ | ✅ | ✅ | ✅ | ||
| all.dns.mullvad.net | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
IP-Addres and Ports
The Table below shows the iP-Addres that you need to configure some dns resolvers.
| Hostname | IPV4 Address | IPv6 Address | Doh Port | Port dowry |
|---|---|---|---|---|
| dns.mullvad.net | 194.242.2.2 | 2A07: E340 :: 2 | 443 | 853 |
| adblock.dns.mullvad.net | 194.242.2.3 | 2A07: E340 :: 3 | 443 | 853 |
| base.dns.mullvad.net | 194.242.2.4 | 2A07: E340 :: 4 | 443 | 853 |
| extended.dns.mullvad.net | 194.242.2.5 | 2A07: E340 :: 5 | 443 | 853 |
| all.dns.mullvad.net | 194.242.2.9 | 2A07: E340 :: 9 | 443 | 853 |
These Ips can only be used with dns resolvers that support doh or dot, not with dns over udp/53 or tcp/53.
How to use this service
Web Browsers
Below You Can Find Configuration Instructions for Different Web Browsers and Operating Systems.
Mullvad Browser
The Mullvad Browser Uses The Mullvad DNS Service (Without Content Blockers) by Default. To change it to one of the options aboo, follow these instructions:
- Click on the Menu Button in the Top Right Corner and Select Setings.
- In the Search Box, type “dns“, then click on the Setings. Button in the Result. If you can not see the button then make the Browser Window Wider or Use the Horizontal Scroll Bar and Drag it to the right.
- In the Bottom Under “use provider” select Custom In the Drop-Down List.
- In the text field that appears, paste one of the following:
- https: // dns.mullvad.Net/DNS-Query
- https: // adblock.dns.mullvad.Net/DNS-Query
- https: // base.dns.mullvad.Net/DNS-Query
- https: // extended.dns.mullvad.Net/DNS-Query
- https: // all.dns.mullvad.Net/DNS-Query
- Click on OK.
Firefox (desktop version)
- Click on the Menu Button in the Top Right Corner and Select Setings.
- Click on Privacy & Security In the Left Column.
- Scroll Down to the Bottom.
- Under Enable Secure DNS Using select Max protection.
- Under Choose Provide Click on the drop down list and select Custom.
- In the text field that appears, paste one of the following, then press Enter on your keyboard.
- https: // dns.mullvad.Net/DNS-Query
- https: // adblock.dns.mullvad.Net/DNS-Query
- https: // base.dns.mullvad.Net/DNS-Query
- https: // extended.dns.mullvad.Net/DNS-Query
- https: // all.dns.mullvad.Net/DNS-Query
Chrome / Brave / Edge
- Open The Setings.
- Click on Privacy and Security (in chrome, brave) or Privacy, Search, and Services (in edge).
- Click on Security (in chrome, brave).
- Enable Use Secure DNS.
- Select with: Custom (in chrome, brave) or Choose A Service Provider (in edge).
- Enter one of the following and press tab on the keyboard:
- https: // dns.mullvad.Net/DNS-Query
- https: // adblock.dns.mullvad.Net/DNS-Query
- https: // base.dns.mullvad.Net/DNS-Query
- https: // extended.dns.mullvad.Net/DNS-Query
- https: // all.dns.mullvad.Net/DNS-Query
- If it knows “please verify that this is a valid provider or try again later” then was at times.
Android 9 and Later
Follow these steps to use dns over tls:
- Open the Android Setings app.
- Tap on Network & Internet.
- Tap on Private DNS.
- Select Private DNS Provider Hostname.
- On the input line, enter one of these:
- dns.mullvad.net
- adblock.dns.mullvad.net
- base.dns.mullvad.net
- extended.dns.mullvad.net
- all.dns.mullvad.net
- Tap on Save.
If Android is unable to connect to the dns then the dns server that you are road to are likely too far away and the latency is prohibitive. In this case it will not work.
iOS and iPados
We Provide DNS Configuration Profiles for Apple Devices.
- Open Safari and Go To Our Github Restity.
- Tap on eith base gold extended (The other profiles are currently expired).
- The profiles are available in two versions (Doh and Dot). Tap on eith one.
- Tap on View Raw.
- Tap on Allow to download the profile.
- Tap on Closed.
- Open The Setings app.
- In the Left Column, Scroll to the Top and Tap On Profile Downloaded.
- Tap on Install.
- Enter your iphone/iPad passcode.
- Tap on Install.
- Tap on Install.
- Tap on Therefore.
You can view, changes and remore installed configuration profiles in the Setings app in General > VPN, DNS & Device Management.
Operating Systems
Windows 11
- Open The Setings app.
- Click on Network & Internet In The Left Side.
- Click on Wireless gold Ethernet Depending on which one you use. You can Tell by the icon in the top which say “�� connected”.
- If you click on wi-fi then click on Hardware Properties and proceed to the next step. If you click on Ethernet then just procedure to the next step.
- Click on the Edit Button Next To DNS Server Assignment.
- Select Manual In the Drop-Down List.
- Enable IPV4.
- In the Prefered DNS field, enter the IP Address For the dns option that you want to use, for example 194.242.2.4.
- 194.242.2.2 – https: // DNS.mullvad.Net/DNS-Query
- 194.242.2.3 – https: // adblock.dns.mullvad.Net/DNS-Query
- 194.242.2.4 – https: // base.dns.mullvad.Net/DNS-Query
- 194.242.2.5 – https: // extended.dns.mullvad.Net/DNS-Query
- 194.242.2.9 – https: // all.dns.mullvad.Net/DNS-Query
- Under DNS Over https, select On (manual template) In the Drop-Down List.
- Under DNS Over https Template Enter the Address Next to the Ip that you selected before, for Example https: // base.dns.mullvad.Net/DNS-Query.
- Click on Save.
- Check in the network details in the same window if you get an IPv6 Address from your internet provider. In that click on the Edit Button Next To DNS Server Assignment again.
- Scroll Down to the Bottom and Enable Ipv6.
- Scroll down again and in the Prefered DNS field, enter the IPv6 Address For the dns option that you want to use, for example 2A07: E340 :: 4.
- 2A07: E340 :: 2 – https: // DNS.mullvad.Net/DNS-Query
- 2A07: E340 :: 3 – https: // adblock.dns.mullvad.Net/DNS-Query
- 2A07: E340 :: 4 – https: // base.dns.mullvad.Net/DNS-Query
- 2A07: E340 :: 5 – https: // extended.dns.mullvad.Net/DNS-Query
- 2A07: E340 :: 9 – https: // all.dns.mullvad.Net/DNS-Query
- Under DNS Over https, select On (manual template) In the Drop-Down List.
- Under DNS Over https Template Enter the Address Next to the Ip That You Selected, for Example https: // base.dns.mullvad.Net/DNS-Query.
- Click on Save.
- If you sometimes uses wi-fi and sometimes use ethernet then go back to step 1 and add the same setings for the other network. Otherwise Make Sure That The Other Network is disconnected Complely to Prevent Windows from Using the DNS from.
macos
This apps to macOS 13 Ventura and Newer. For old versions, ferment to the macOS user guide.
- Open Safari and Go To Our Github Restity.
- Click on Either base gold extended (The other profiles are currently expired).
- The profiles are available in two versions (Doh and Dot). Click on EITHER ONE.
- Click on View Raw.
- Click on Allow to download the profile.
- Open The System Settings app.
- In the Left Column, Click on Privacy & Security.
- On the right side, scroll to the bottom and click on Profiles.
- Double-Click on the Mullvad Encrypted DNS profile that you downloaded.
- In the Bottom Left Corner, Click on Install.
- Enter Your MacOS Login Password and Click on OK.
You can view and Remove Installed Configuration Profiles in the System Settings app in Privacy & Security > Profiles. If you have more Than one profile added then macos Seems to Use Only the Last One That You Installed. If you Remove a Profile then It Appears that it will not use any of the other profiles.
Linux (Ubuntu and Fedora)
These instructions use systemd-resolved.
- OPEN A TERMINAL.
- Make sure that systemd-resolved is enabled by running this command:
Sudo Systemctl Enable Systemd-Resolved - Open the Settings App and Go to Network. Click on the Settings Icon for your Connected Network. On the IPV4 and IPv6 tabs, turn off automatic next to dns, and leave the dns field white, then click on apply. Disable and Enable The Network Using The On/Off Button To Make Sure It Takes Effect.
- Edit The Following File With Nano Or Your Favorite Text Editor:
Sudo nano/etc/systemd/resolved.confused
Add the following Lines in the Bottom Under [Resolve]. Select a dns option by Removing the First # in Front of the One You Want To Use:
#DNS = 194.242.2.2#DNS.mullvad.net
#DNS = 194.242.2.3#Adblock.dns.mullvad.net
#DNS = 194.242.2.4#base.dns.mullvad.net
#DNS = 194.242.2.5#Extended.dns.mullvad.net
#DNS = 194.242.2.9#all.dns.mullvad.net
Dnssec = no
DNSOVERTLS = Yes
Domans = ~. - Save the File by Pressing Ctrl + O and then Enter, and then Ctrl + X on your Keyboard.
- Create a Symbolic Link to the File Using the Following Command in the Terminal:
Sudo LN -SF/RUN/SYSTEMD/Resolve/Stub -Resolv.Conf /etc /resolv.confused - Restart Systemd-Resolved by Running this Command:
Sudo Systemctl Restart Systemd-Resolved - Restart NetworkManager with this command:
Sudo Systemctl Restart NetworkManager - VERIFY THE DNS SETINGS With:
Resolvectl Status
In Case it doesn’t work, Change to this Setting in/etc/Systemd/Resolved.conf:
How do I Know It’s Working?
After you have followed the instructions on, go to https: // mullvad.net/check. You should have no dns leaks. Click on “no dns leaks” for details; The server that is listed should have “dns” in its names, for examination “se-mma-dns-001.mullvad.net”.
DNS Server Rentals
The nearest dns server will be used. If one server is down, the next -closest will be used and so on.
Keep in mind that nearest is in terms of networking hops, this can differential your isp and their
Connectivity to Our Hosting Providers.
Our dns servers are located in:
Australia- Germany
- Singapore
- Swowl
Switzerland- United Kingdom
- United States (NYC,
Daland lax).
How the Content Blocking Works
Mullvad Curates A Collection of “Theme” Lists Whose Content is Source from Publicly Available Block Lists.
When the client queries for a hostname that matches an item in the block list our resolver Simply Lies to the Customer and Says that the Hostname does not exist.
This Means that What Whatever Content was attempted to be loaded by the Browser is not loaded and is therefore not Shown on the Screen.
For more information on which sleeps are blockled by which lists and which community lists make up the curated mullvad lists please our github.
DNS content blocking can not block all ads and trackers. For example it can not block youtube ads. To block more ads and trackers in your web browser we recommend using the ublock origin extension. This is included in the Mullvad Browser.
Notes
Earlier Versions of this Guide contained References to Doh.mullvad.net and dot.mullvad.net. These hostnames has been replacement with the common dns.mullvad.net hostname and are subject to future deprecation. We urge all users to use the new hostnames that include dns.mullvad.net.
The Following IPS Are not used anymore: 193.19.108.2 and 193.19.108.3.
Mullvad
- About
- Help
- Servers
- Prices
- Blog
- What is confidentiality ?
- Why Mullvad VPN ?
- What is a VPN ?
- Download the customer
- Press
- Job
Avoid DNS leaks
DNS leaks represent a serious threat to your online private life. Using the Proton VPN VPN Tunnel, your online activities and your data remains private, safe and permanently protected:

What is a DNS leak and how to avoid it ?
When you go to a website, your browser sends requests to the domain name system (DNS) to find the web page you want to visit. The DNS translates the domain names that we use (like ProtonVPN.com) in IP addresses that computers use. If these DNS requests are not encrypted, your Internet service provider (ISP), among others, can monitor your activities. Proton VPN takes several measures to ensure that your DNS requests are never exposed.
Your DNS requests are encrypted
Our VPN applications automatically quantify your DNS requests and include them in the VPN tunnel: they cannot therefore be intercepted or read by third parties during their transmission.
We are exploiting our own DNS servers
A Proton VPN server has a DNS server that takes care of processing your DNS requests. No third party has a clear access, including your Internet access provider (ISP) and your DNS supplier.
DNS leakage test
You can check that your VPN connection is secure by logging into a server, going to a DNS leakage test website (New Window) and doing their standard or in -depth test. If the results show DNS servers that do not belong to your Internet access provider (ISP), your VPN connection is secure.

The VPN you can trust to protect your privacy
Based in Switzerland
Proton VPN was designed by the team from Proton Mail. We are based in Switzerland, a country located outside the courts of the United States and the European Union, which is known for its strict data protection and privacy laws.

Strong encryption
Each VPN Proton connection is encrypted using AES-256, an encryption algorithm which has no known vulnerability and which is resistant to attacks by force brute force.

On all your devices
Our Proton VPN applications are easy to use and available on all platforms, including iPhone, Android, Mac, Windows, Linux, Fire TV Stick, Chromebook, Android TV and others still.
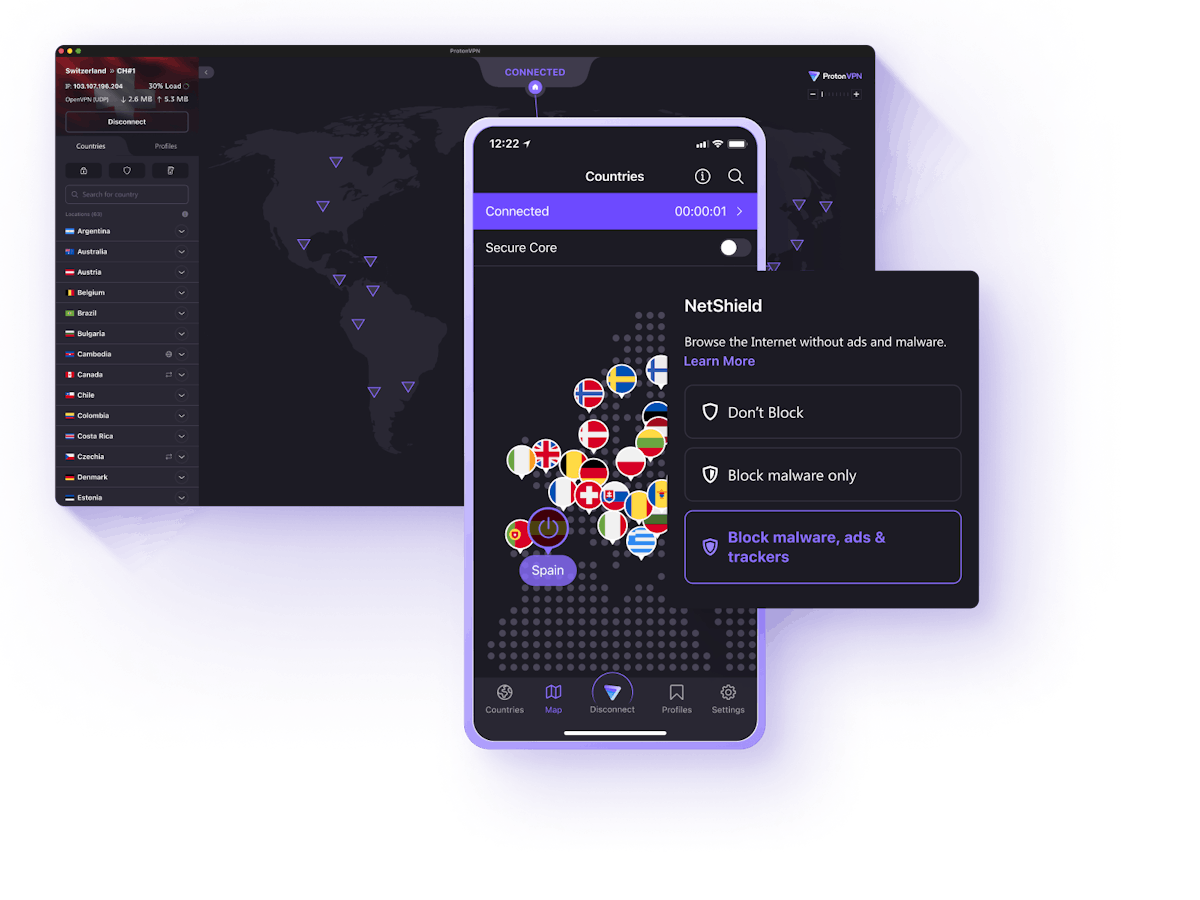
The only secure, private and unlimited VPN
Audited by independent experts
Proton VPN was independently audited by security experts. You will find their reports on our website.
Trustworthy
Proton VPN is used by journalists, activists and millions of people around the world to circumvent censorship and protect their activities online.
VPN Accelerator
Free and available for all those who use Proton VPN, our exclusive VPN Accelerator technology can improve speeds by more than 400 %.
Ultra fast connection
Take advantage of fast navigation sessions with Proton VPN, up to 10 Gbit/s, and use our VPN Accelerator technology to improve long -distance connections performance.
Netshield advertising blocker
Netshield protects your device and accelerates your navigation by blocking advertising, trackers and malware.
Streaming worldwide
Access content blocked geographically on streaming sites like Netflix and Amazon Prime Video, whatever the place you are.
VPN without newspapers
Proton VPN does not keep any metadata newspaper which could compromise your confidentiality.
World server network
Proton VPN has more than 2,900 servers distributed in more than 65 countries and you can connect up to 10 devices.
sweep to the right or left to discover all the values
Download a secure VPN
- TOR VIPN
- No advertising, no tracker, no newspaper
- Prevents DNS and IPv6 leaks
- Complete disk encryption on all servers
- Free and unlimited
frequently asked Questions
How is a DNS leakage ?
Your DNS requests are a recording of the websites you have visited. If they are not encrypted through a secure tunnel, they can be leaks and be exposed to attackers and your Internet access provider (FAI).
How to know if there have been DNS leaks ?
The easiest way to check if there have been DNS leaks is to go to this website (New Window) and carry out tests. We advise you to carry out two tests: one before the activation of Proton VPN and one after. As Proton VPN prevents third parties from seeing your DNS requests, the results should not be the same.
Which solves DNS requests when using Proton VPN ?
In the case of a connection with Proton VPN, all your DNS requests are encrypted, go through our VPN tunnel and are resolved by our DNS servers. No third party has access to your DNS requests. We do not keep any newspapers of your DNS requests.
How to correct a DNS leak ?
If you notice a DNS leak using Proton VPN, signal it immediately to our security team with this form.
- Free VPN
- VPN servers
- VPN for streaming
- VPN for Netflix
- VPN Secure Core
- Start well
- Download the VPN
- VPN for Windows
- VPN for Mac
- VPN for Android
- VPN for iOS
- VPN for Linux
- VPN for Chrome
- VPN for Firefox
- Legal notices (New Window)
- Privacy Policy
- General conditions of use (New Window)
- Transparency report
- Threat model
- a b u s e @ & x70 r o t n n v p n . c o &
- About Us
- VPN Proton Status (New Window)
- Support
- Work at Proton (New Window)
- Open source
- Press kit (New Window)
- Twitter (New Window)
- Reddit (New Window)
- Linkedin (New Window)
- Instagram (New Window)
- Facebook (New Window)
- Mastodon (New Window)
- YouTube (New Window)
- Help & support: Contact the support
- Company: Contact the sales team
- Partnership: Contact the partnership team (New Window)
- Media: m e d i a @ p r o t o & x6e v p n . c c
- Security: s e c u r i t y @ r o t o n v p #X6F m
- Abus: a b u s e @ p r o o n v p n . c c &#



