Configure postgresql extensions | Cloud SQL for PostgreSql | Google Cloud, Google Bard can now connect to Gmail, Docs, Maps: how it works
Google Bard can now connect to Gmail, Docs, Maps: how it works
Last update on 2023/09/05 (UTC).
Configure postgreSql extensions
You can extend postgreSql by grouping SQL objects in a package to use them as a unit. This page contains information on the configuration of postgresql extensions compatible with Cloud SQL.
Use postgreSql extensions
You can only install extensions compatible with Cloud SQL. For more information, see the PostgreSql Extensions section Compatible with Cloud SQL.
Noticed : You can only install extensions on the main instance, not on the duplicated instance with reading access. Once installed, the extension is replicated on the duplicated body with reading access.
Install an extension
Before using an extension, install it by proceeding as follows:
- In the PSQL tool, run the Create Extension command.
Conditions required for superuser rights
In Cloud SQL, extensions can only be created by users with the Role Cloudsqlsuperuseruse . When you create a postgreSql instance, the default postgre user is created automatically (but you must define their password). The default postgres user has the Cloudsqlsuperuser role . For more information, see the page about PostgreSql users.
Noticed : If you import a database containing an extension created by a personalized user, you cannot delete the user without deleting the entire imported database.
Connections between databases
To connect, target instances must be in the same VPC network as the connection body.
In Google Cloud Console, you cannot choose the button Authorize only SSL connections For cluster instances. In addition, to connect to databases within the same instance, you cannot define the host on “Localhost” or on 127.0.0.1 . You must use the IP address indicated for your instance in Google Cloud Console.
Request assistance for a new extension
You cannot create your own extensions in SQL Cloud.
For an assistance request regarding an extension, click on +1 on the report, or create a new problem. To obtain the list of problems reported regarding Cloud SQL and obtain information on the creation of problems, see the Search section or create problem reports and product features requests.
POSTGRESQL extensions compatible with SQL cloud
For more information on using a specific extension, follow the link to the documentation appearing in one of the tables below.
Assistance concerning PostgreSql extensions with Cloud SQL is divided into several categories:
- Postgis extensions
- Data type extensions
- Language extensions
- Various extensions
Postgis
Postgis 3 extension.0 is compatible with Cloud SQL for PostgreSql for all major versions.
The following table contains the versions of the postgis extension for each version of SQL cloud for PostgreSql:
| SQL Cloud version for PostgreSql | Postgis extension |
| PostgreSql 9.6 | 2.3.11 |
| PostgreSql 10 | 2.4.9, 3.1.4 |
| PostgreSql 11 | 2.5.5, 3.1.4 |
| POSTGRESQL 12 | 3.1.4 |
| PostgreSql 13 | 3.1.4 |
| PostgreSql 14 | 3.1.4 |
For a major specific version of PostgreSql, in the Create Extension command, you can specify a version of the postgis extension using the version version .
The postgis extension includes the following elements:
- postgis
- Postgis_Raster
- Postgis_sfcgal
- POSTGIS_TIGER_GEOCODER
- Postgis_topology
- Address_standardizer
- Address_standardizer_data_us
For more information, see the PostGis Installation section (installation of PostGis).
In addition, Cloud SQL for PostgreSql includes version 3.3.0 of the pgrouting extension, which extends postgis. The pgrouting extension improves geospatial treatment via routing and network analysis.
You can upgrade manually Postgis and the associated extensions to their latest version. To find out more about upgrading your postgis extensions, see the PostGi Upgrade page.
Data type extensions
| Extension | Description |
| Btree_gin | Provides examples of classes of GIN index operators which implement behavior equivalent to a B-Tree index. Cloud SQL for PostgreSql 9.6 Use version 1.0. Postgresql 10 uses version 1.2. All other versions use version 1.3. |
| Btree_gist | Provides classes of GIST index operators which implement behavior equivalent to a B-Tree index. Cloud SQL for PostgreSql 9.6 Use version 1.2. PostgreSql 10, 11, 12 and 13 use version 1.5. Postgresql 14 uses version 1.6. |
| chkpass | Implements a chkpass data type designed to store encrypted passwords. Cloud SQL for PostgreSql 9.6 and 10 use version 1.0. Not compatible with other versions. |
| citext | Provides a type of CITEXT character chain not sensitive to breakage. Cloud SQL for PostgreSql 9.6 Use version 1.3. Postgresql 10 uses version 1.4. Postgresql 11 uses version 1.5. Postgresql 12, 13 and 14 use version 1.6. |
| cube | Implements a type of cube data to represent multidimensional cubes. Cloud SQL for PostgreSql 9.6 and 10 use version 1.2. Postgresql 11 uses version 1.3. Postgresql 12 and 13 use version 1.4. Postgresql 14 uses version 1.5. |
| hstore | Implements the HSTORE data type to store key/value pairs sets within a single postgreSql value. Cloud SQL for PostgreSql 9.6 and 10, use version 1.4. Postgresql 11 uses version 1.5. Postgresql 12 uses version 1.6. Postgresql 13 uses version 1.7. Postgresql 14 uses version 1.8. |
| Isn | Provides data types for certain international product numbering standards. Cloud SQL for PostgreSql 9.6 and 10 use version 1.1. All other versions use version 1.2. |
| IP4R | Provides data types for IPV4/V6 addresses, IP address beaches and compatibility with indexes. Cloud SQL for Postgresql uses version 2.4. |
| ltree | Implements an LTree data type to represent the data labels stored in a hierarchical structure in the form of a tree. Cloud SQL for PostgreSql 9.6, 10, 11 and 12 use version 1.1. Postgresql 13 and 14 use version 1.2. |
| lo | Assistance for the management of large objects (also called LO or Blob). Cloud SQL for Postgresql uses version 1.1. |
| PostgreSQL-HLL | Introduces a new type of data, HLL, which is a hyperloglog data structure. Also see the PostgreSql-HLL section in this document. Cloud SQL for Postgresql uses version 2.16. |
| prefix | Provides a prefix correspondence as well as compatibility with indexes. Cloud SQL for Postgresql uses version 1.2.0. |
Language extensions
| Extension | Description |
| plpgsql | Loadable procedural language to create functions, procedures and triggers. You can also use this language to execute code directly in do blocks. Cloud SQL for Postgresql uses version 1.0. |
| PLV8 | Provides a procedural language to activate JavaScript. Cloud SQL for Postgresql uses version 3.1.2, which uses version 9.9 of the JavaScript V8 engine. |
Various extensions
- Cloud SQL for PostgreSql 9.6 Use version 1.1.4 Pgaudit.
- Cloud SQL for Postgresql 10 uses version 1.2.3 Pgaudit.
- Cloud SQL for Postgresql 11 uses version 1.3.3 Pgaudit.
- Cloud SQL for Postgresql 12 uses version 1.4.2 of Pgaudit.
- Cloud SQL for Postgresql 13 uses version 1.5.1 of Pgaudit.
- Cloud SQL for Postgresql 14 uses version 1.6.1 of Pgaudit.
The values you can define for audit news files for all versions of Pgaudit are Read, Write, Function, Role, DDL, MISC and ALL . For versions 1.4.2 to 1.6.1, you can also define the value of misc_set .
For more information on using this extension with SQL Cloud, see the PostgreSql audit page using Pgaudit.
Created and manages DB2 or Oracle type temporary tables in a postgreSql database.
Cloud SQL for Postgresql uses version 2.9.0.
Open Source extension to store and search for continuous vector representations in PostgreSql databases.
Cloud SQL for Postgresql uses version 0.4.2
Hide or replace personal or sensitive information from a postgreSql database to find out more, see the postgreSql_anonyMizer section.
Cloud SQL for Postgresql uses version 1.0.0.
Find out more about certain postgreSql extensions
This section describes in more detail some of the postgresql extensions compatible with the above tables.
Aut_explain
To start using this extension on an instance, define the Cloudsql option.enable_auto_explain on on . To find out more about the configuration of options and to discover the options compatible with this extension, see the Configure Database Options page.
In addition, for a user with the Cloudsqlsuperuseruse role (only), you can use the LOAD command to load this extension during a session.
dblink
In a database session, you can use this extension to connect to PostgreSql databases and run requests.
Currently, this extension operates for two SQL Cloud instances with private IP connectivity within the same VPC network, or for databases crossed within the same instance.
Noticed : In Cloud SQL, it is not possible to use customer certificates with DBLINK.
For more information, see the DBLINK section in the postgreSql documentation.
Use DBLINK to connect with a password
To connect to databases or to connect to the same instance as another user, you must specify a password. Here is a code extract as an example (not to be used in production):
Select * from dblink ('dbname = name port = 1234 host = host user = user password = password', 'select id, name from table' \) as t (id int, text text); Otherwise, to configure only a connection, here is another example of code (not to be used in production):
Select dblink_connect ('dbname = dblinktest user = postgres host = name_or_ip password = xxx'); Connect without password using DBLINK
To connect to the same instance using the identity of the same user, you can connect without password. Example :
- Define the following database indicator to activate local connections without password.
Cloudsql.allow_passwordless_local_connections - Connect without specifying host, which implies a connection to the same instance. Here is an example :
Select * from dblink ('dbname = finance user = alice', 'select incomes from income') as returned (incomes integer); The result should look like this:
Income -------- 1000 (1 Row) In addition, to connect to other databases within the same instance, you cannot define the host on “Localhost” or on 127.0.0.1 . You must use the IP address indicated for your instance in Google Cloud Console.
Also consult the postgres_fdw and PL/proxy sections in this document.
page
This extension inspects the content of the database pages at a lower level. To find out more, see the Pageins Respect section in the postgreSql documentation.
pg_bigm
This extension activates full text research and allows the use of a bigram index for faster full text search.
To start using this extension on an instance, define the Cloudsql option.enable_pg_bigm on on . The following options are also accepted:
- pg_bigm.Enable_recheck
- pg_bigm.gin_key_limit
- pg_bigm.similarity_limit
To find out more about the definition of options and to discover the options compatible with this extension, consult the Configure Database options.
pg_cron
To start using PG_cron on an instance, define the Cloudsql option.enable_pg_cron on on . To find out more about the definition of options and to discover the options compatible with this extension, consult the Configure Database options.
The tasks are configured as a background calculation nodes. You may therefore have to use the standard postgreSql techniques (such as the Max_Worker_Processes option) to adjust the number of calculation nodes in the background.
For this extension, Cloud SQL is compatible with the calculation node mode in the background, but not with the LIBPQ interface. Therefore, this extension does not require direct authentication.
pgfincore
This extension contains functions to manage the pages in the cache memory of the operating system disk from Postgresql. For more information, see the documentation dedicated to Pgfincore.
pg_freespacemap
This extension examines the free space map (FSM, Free Space Map). To find out more, see the PG_FREESPACEMAP section in the postgreSql documentation.
pg_hint_plan
To start using this extension on an instance, define the Cloudsql option.enable_pg_hint_plan on on . To find out more about the configuration of options and to discover the options compatible with this extension, see the Configure Database Options page.
Otherwise, for a user having only the Cloudsqlsuperuser role, you can use the LOAD command to load this extension during a session.
pg_partman
This extension allows you to create and manage sets of Tables based on the hour and the series.
In Cloud SQL, this extension does not include the calculation node in the background for automatic maintenance of partitions. Instead, you can for example use Cloud Scheduler to orchestrate maintenance by calling maintenance functions at regular intervals.
PG_PROCTAB
Here are the steps to follow to use the PG_PROCTAB extension to activate the PG_TOP utility:
- In the PSQL tool, run the Create Extension command for PG_PROCTAB.
- Download and run PG_Top.
- When you connect to an SQL Cloud Instance for Postgresql, add the -r option so that you can connect to a remote database and get metrics.
The following metrics at the instance scale, which are included in the result, include use by other agents and services of the body:
- Medium load
- States of processors (% user, Nice, System, Inactive and Iowait)
- Memory (used, free and chatting)
pg_repack
This extension allows you to delete bulky data from tables and indexes. You can possibly use this extension to make an online cluster (classify the tables by cluster index). For more information, see the documentation dedicated to PG_REPACK. In addition, to use this extension in SQL Cloud, a special procedure is necessary in order to add rights to a user.
If a user does not have the Cloudsqlsuperuser role wishes to use an extension, you must grant him the rights of Cloudsqlsuperuseruse . To find out more, consult conditions required for super-user rights. The following example uses the Grant command to add the necessary rights.
Example of adding rights
For example, CSUPER1 corresponds to a Cloudsqlsuperuser and TESTDB user is a database belonging to TESTUSER . To create the PG_REPACK extension in TestDB, initially run the following commands:
- Connect to TestDB as a Cloudsqlsuperuseruse user:
PSQL -u CSUPER1 -D TESTDB; Grant testuer to csuper1; Create Extension PG_REPACK; pg_repack -h -d testdb -u csuper1 -K -t t1 Revoke Testuser from Csuper1; The PG_REPACK command can fail with the following error:
“Error: query failed: SSL SYSCALL ERROR: EOF DETECTED”
If this error occurs, try to define a smaller value for TCP keepalive messages, then run the PG_REPack command . To find out more, see the Deadline before expiration of connections (from Compute Engine).
pgtt
To start using this extension on an instance, define the PGTT option.Enabled on on . To find out more about the settings of indicators and to discover the indicators compatible with this extension, consult the page Configure database indicators.
pg_visibility
Allows you to examine the visibility card (VM, Visibility Map) and visibility information at the page of a table. To find out more, see the PG_visibility section in the postgreSql documentation.
PL/PROXY
This extension is a procedural languages manager authorizing remote procedural calls between postgreSql databases, with optional segmentation.
For more information, see the PL/Proxy documentation.
To connect, target instances must be in the same VPC network as the connection body. In Google Cloud Console, you cannot choose the button Authorize only SSL connections For cluster instances.
In addition, to connect to other databases within the same instance, you cannot define the host on “Localhost” or on 127.0.0.1 . You must use the IP address indicated for your instance in Google Cloud Console.
Also consult the postgres_fdw and dblink sections in this document.
PostgreSql_anonymizer
To start using this extension on an instance, define the Cloudsql option.Enable_anon on on . To find out more about the settings of indicators and to discover the indicators compatible with this extension, consult the page Configure database indicators.
postgres_fdw
This extension makes it possible to expose the tables of other postgreSql databases as “foreign” tables in the current database. These tables are then available, a bit as if they were local tables. For more information, see the postgres_fdw section in the postgreSql documentation.
This extension operates for two SQL Cloud instances with private IP connectivity within the same VPC network, or for databases crossed within the same instance.
In addition, to connect to other databases within the same instance, you cannot define the host on “Localhost” or on 127.0.0.1 . You must use the IP address indicated for your instance in Google Cloud Console.
In addition, in Google Cloud Console, you cannot choose the button Authorize only SSL connections For cluster bodies that store foreign data. Only a Cloudsqlsuperuser user can own a Wrapper of foreign data postgres_fdw.
Also consult the PL/Proxy and Dblink sections in this document.
PostgreSQL-HLL
This extension introduces a new type of data, HLL, which is a hyperloglog data structure. For more information, see the documentation dedicated to PostgreSql-Hll.
Comment
Unless otherwise indicated, the content of this page is governed by a Creative Commons Assignment 4 license.0, and code samples are governed by a Apache 2 license.0. For more information, see the rules of the Google Developers site. Java is a registered trademark of Oracle and/or its affiliated companies.
Last update on 2023/09/05 (UTC).
Google Bard can now connect to Gmail, Docs, Maps: how it works
The conversational agent is now able to combine information from different Google tools and incorporates a source verification system.
José Billon / published on September 19, 2023 at 4:31 p.m
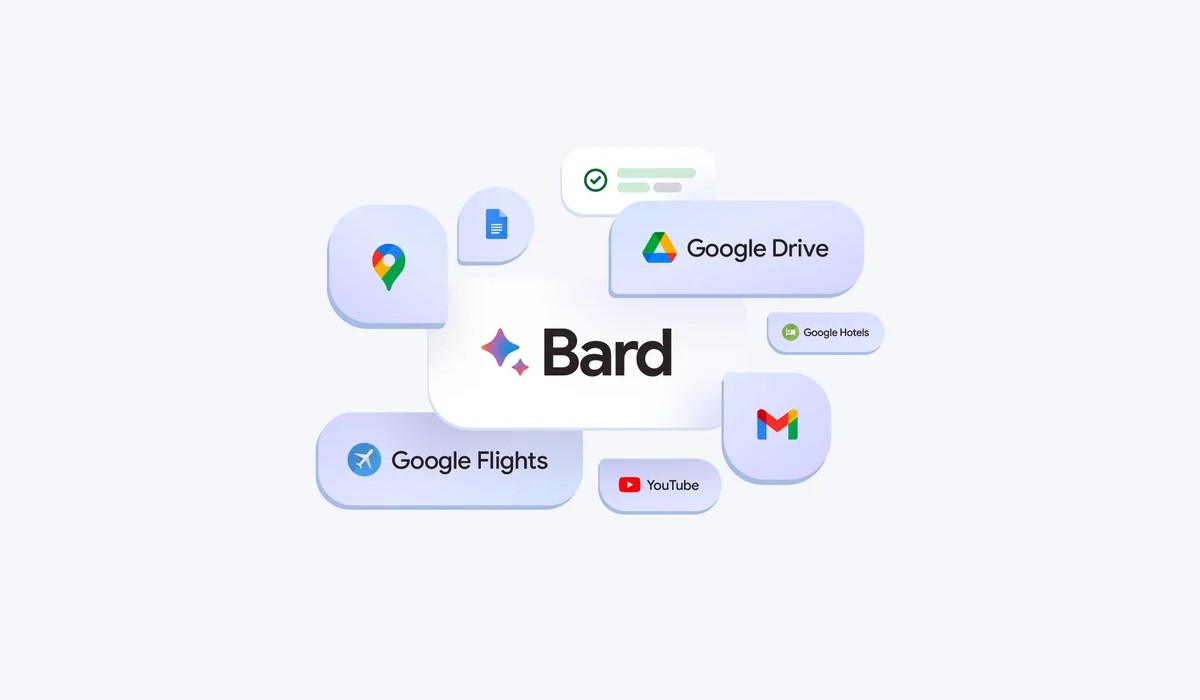
In a post published blog this Tuesday, September 19, Google announces new products for its Chatbot Google Bard. The Chatgpt competitor, who had not been updated since July 13, has extensions allowing him to connect to other Google products and an option to verify sources. These additions, which follow updates of the Palm 2 model, are only accessible for English uses.
Extensions for Google Bard
Google Bard extensions now allow users to “Find and display relevant information from Google tools”, Like Gmail, Docs, Drive, Google Maps, YouTube or Google Hotels. Concretely, Bard is able to seek information within each service, and to combine it to provide an adapted response.
For example, if you plan a trip to the Grand Canyon (a project that occupies many tabs), you can now ask Bard to extract from Gmail the dates that are suitable for everyone, to consult the information in real time on Flights and hotels, get Google Maps’ route to the airport, […] all in a single conversation.
In addition, Google undertakes to protect personal information: extensions for Google Workspace will not use your content from Gmail, Docs and Drive for targeted advertising or to train the model.
Google Bard checks its answers
On its interface, Google Bard always indicates that it is in the experimental phase. Indeed, when it was launched, the chatbot announced power “Sometimes getting wrong”, what we had been able to confirm during our test. To ensure users of the veracity of the information it transmits, AI now incorporates a function double check, which offers the possibility of accessing concordant and contradictory sources relating to information transmitted in the responses.
Concretely, if you press the button Answer (Google logo), the chatbot assesses if there is content on the web to corroborate its answer. The sentences highlighted in green offer supporting sources, while the sentences highlighted in orange offer divergent sources.
Extensions for Google Chrome can recover your passwords in clear !

From a simple Google Chrome extension, it is possible to recover in clear the passwords that you enter on many popular sites. Security researchers have highlighted this weakness in a report. Let’s do a check in.
A team of researchers from the University of Wisconsin-Madison has posted a new technical report which shows that a legitimate extension installed from the web store chrome within a browser is able to steal sensitive information. THE principle of the least privilege not being applied by developers in many extensions, including some popular, makes them able toAccess the information entered in a website forms. This can allow the extension of Recover in clear the user’s user identifier and password.
In fact, researchers explain that the problem is linked to the fact that developers give extensions Unlimited access to the Dom tree sites. Even if behavior is not the same on all sites, with certain forms, The data entered is visible in the source code and extensions can recover them. To this is added the fact that The extension can abuse the Dom API to directly extract the information entered as the user enters it.
To provide an additional safety layer, the majority of browsers use The Manifest V3 protocol introduced to Google Chrome and which prevents extensions from carrying out certain actions. However, it is insufficient and ineffective against content scripts.
Thus, the extension developed by developers who presents himself as an assistant based on GPT is capable of Recover sensitive information by abusing the HTML source code of the page, CSS beacons and JavaScript elements. This extension does not include any malicious code and It conforms Manifest V3 Because it does not load code from external sources. Therefore, it was approved by Google and was put online on the Chrome Web Store.
The most popular sites are vulnerable
According to the tests carried out by the researchers, the majority of the top 10,000 world sites are vulnerable. About 1,100 sites store user passwords in the form of a clear text in html dom. In addition, 7,300 sites are vulnerable to data extraction via DOM API access.
This weakness does not only affect Google Chrome because other browsers use the chromium base.
Here are some examples : gmail.com, facebook.com, cloudflare.Com, Amazon.com.

At the same time, About 17,300 extensions of the web store chrome (ie 12.5 %) have the authorizations necessary to extract this sensitive information. This is all the more disturbing since 190 extensions (some with more than 100,000 downloads) already store this information in variables. Which suggests that certain extensions already exploit this security problem.
Share this article 




- ← Previous in Europe, Microsoft 365 subscriptions will be sold with or without Microsoft Teams
- Microsoft will force the upgrade on the machines still under Windows 11 version 21:2:2 am Next →
Florian Burnel
System and network engineer, Co-founder of IT-Connect and Microsoft MVP “Cloud and Datacenter Management”. I want to share my experience and my discoveries through my articles. Generalist with a particular attraction for Microsoft solutions and scripting. Good reading.
Florian has 4966 posts and counting.See All Posts by Florian



